The EU Cyberwar on People & the Web
By Gabriel
Published: Nov 06 2023
Cyberwar
European Union
Government
Digital ID
Surveillance
The largest institutions from governments, alliances, and multi-national corporations are all wrestling for control over total digital dominance of the public. Your own access to information, and control over your data are both important objectives to these organizations. This battle over people’s digital lives is not without it’s consequences. There are disastrous possibilities if any group manages to secure surveillance and/or control over everyone’s online communications, transactions, and information.
This problem isn’t new. Even back in 2002, Stephan Engberg was one of many warning about how knee-jerk approaches to digital security can end up creating new unnecessary risks. From convenience to institutions with control over our lives, there are all kinds of ways in which security and control can be out of the people’s hands. Essential services like banking, communication, and access to necessities can very easily be gated behind “secure” options fraught with problems.
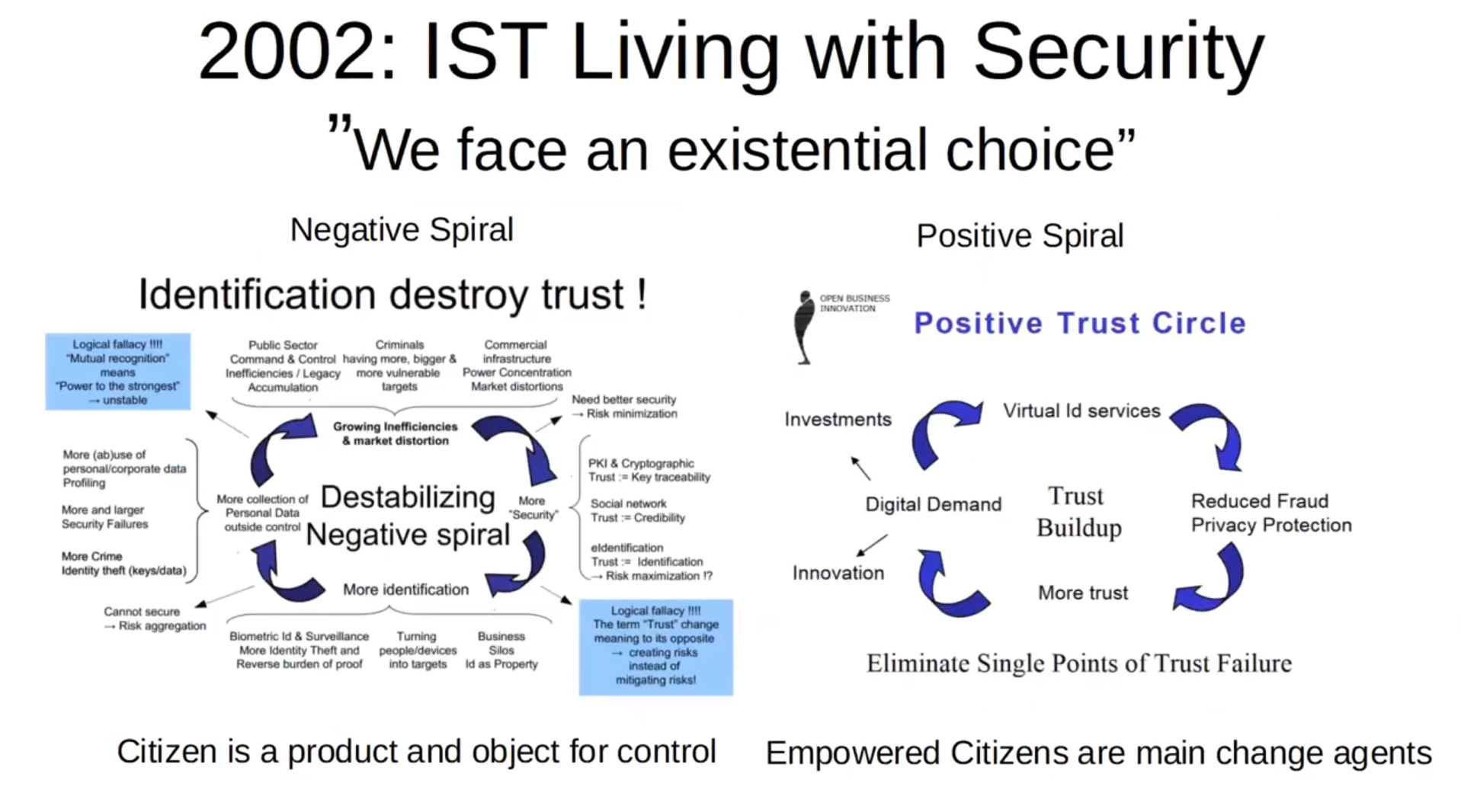
Privacy Engineering Group - Stephan Engberg Source
There is a temptation, to try to build a privacy respecting foundation to build digital identity on. Stephan himself is working on Citizenkey, which aims to make anonymous verification possible, with the possibility of de-anonymization through a trusted third party. As an alternative route to total top-down control and tyranny, this would seem like a decent compromise, but unfortunately there is little reason to believe it would stay that way. The assumption that institutions have the right to treat people like livestock to be tracked is itself the problem.
There is no reason that as our lives are transformed by additional digital options, that we must accept losses of privacy to move forward. This arrogant fallacy merely suits those who want to rent-seek on advances in technology by privatizing (or brokering) control of it. At least while we still can, it’s important to remember that each and every one of us cna choose a different path.
The Poison Pill
The EU recently had to back-off extreme client-side-scanning measures, to much fanfare, even calling it a victory. Repealing merely the most offensive part of legislation that can enable and sanction state overreach is not a long-term solution. As we can see, the EU is already rolling forward with more egregious attacks on people’s privacy.
An open letter signed by Mozilla, and other tech organizations and companies, decries the inclusion of a root certifiate into browsers. A root certificate is a digital file that validates SLL certificates for websites, for any website. If I can place a root certificate on your device (or have it included in your browser) I have the ability to decrypt all of your online traffic. This has been done by despotic regimes to snoop on internet traffic and opens the door to even more egregious acts of online censorship. Not only are the root certificates required, but under the regulations browsers are not allowed to revoke the certificates if they are abused.
It’s great to have organizations like the Linux Foundation, and companies like Cloudflare stand up for our internet security right? Not so fast! All the fanfare about eIDAS 2.0 seems to suspiciously exclude the fact that the regulation itself builds a framework for digital ID. These organizations are merely standing against the worst part of legislation that will undermine digital freedoms. If we can’t trust our governments to not include provisions like the root certificate addition, trusting hem with digital ID is merely another opportunity to exploit the public.
Digital ID
It’s well understood that most internet traffic is bots these days. It’s only becoming harder and harder for us and the controllers to tell who is a person and who is a digital agent acting on someone’s behalf. Surveillance and control of the outside world is still an expensive and violent affair. Digital ID is something that can mitigate both these problems. By forcing you to give up anonymity (or even pseudonymity) in a variety of places, you can be controlled by those who control the system.
During the Covid Crisis vaccine passports functioned as a beta test for Digital ID. Access to all kinds of entertainment and recreation was contingent on having a digital wallet that included your health information, many people lost their employment for lacking one. Far from a hypothetical, China used the health pass system to suppress bank runs. This has given many insight into the abuses that are possible if access to services and essentials is gated behind a programmable identification.
While sympathy for those without vaccine passports wasn’t particularly high where I lived, it’s important to understand what this system does to all of our fundamental rights. For quite some time now, the western world has made civil rights progress by establishing groups that are protected from particular kinds of discrimination. Just as it wasn’t any help to protect people from medical discrimination during the covid crisis, this framework will be wholly inadequate at protecting people from automated individual discrimination.
If the power structure has insight to all of a person’s activities, what they read, and what they say. It becomes easier to oppress particular people for reasons that aren’t attached to a protected class. More and more people’s fundamental rights will be eroded by a constant flow of conjured exceptions to individual rights protections. In the Covid Crisis the discrimination was over health decisions, but the exact same framework could be used towards other ends. One day, a tyrant could use the system to punish those who are neurodivergent, or otherwise deviant from the ideal model citizen. Instead of punishing people for crimes, you can use permissioned control of society to punish individuals for what they are and for particular aspects of their lives.
Slowly, Then All At Once
Bit by bit, people have granted large corporations more and more control over people’s lives. Governments are keenly interested in having an impact on this new source of power. The great challenge is that there may come a time where it is impossible for people within this system to reverse the effects and regain control. Digital IDs being launched voluntarily, is no guarantee that they will remain optional.
From the FAQ
The main novel element offered by the new rules is that everyone will have a right to have a EU Digital Identity Wallet which is accepted in all Member States. But at the same time, there will be no obligation. Users will be able to control what personal data they want to share with online services. While public services and certain private services will be obliged to recognise the EU Digital Identity Wallet, its security features make it attractive for all private service providers to recognise it for services that require strong authentication, creating new business opportunities.
The fundamental issue is if people are willing to let top-down state control be inserted into all aspects of their lives like the internet was. Will people allow their governments to use corporations acting on their behalf, to carry out the same overreach? Will those who truly want to protect individual rights, find ways to help others outside this system? Is it already too late?
What Can We Do?
Right To Be Offline
Accept that there are situations where people shouldn’t be forced to use a particular electronic system or device. Accept that anonymity, especially online, is one of the best ways to protect against total surveillance. Anything that can be done to support those who choose not to be identified, or to refuse interacting with particular systems and services can go a long way.
Pushback
Get connected with people in your jurisdiction and get informed about the state of cyber laws and protections affecting you. A single person writing in to their bought-and-paid for politician isn’t sufficient. This has to be one of the issues that a coalition is built around to find a better direction. Cooperating with others to run your own digital services as a community would be a radical improvement.
Withdraw Your Consent
Don’t make tyranny easier by complying. Anything you can do that adds friction to the process of tracking and controlling everyone’s activity can really make an impact. Choosing to avoid big tech services where possible, or refusing to adopt an “optional” government program can be something that reduces it’s chance of catching off broadly.
More Resources
Sharing is caring!
Please send this post to anyone you think might be interested.
If you haven't already, don't forget to bookmark this site!
You can always subscribe with the RSS feed or get posts sent to your inbox via Substack.
