DIY Cyber Audit
By Gabriel
Published: Sep 30 2023
Operation: Shadow
Privacy
Cybersecurity
Guide
It’s good for people to take their own cybersecurity seriously. It’s a huge topic, and it can be difficult to decide what’s worth starting with, or expending a lot of effort on. This guide is intended to walk you through some of the basic “bare-minimum” steps one would want to take in improving their online security. In addition to pure security goals, this piece aims to emphasize how to reduce your dependency on systems that seize control of your information and workflows. It is my opinion that consolidated power inevitably leads to abused power, therefore one should take an active role in reducing their participating in enabling nefarious entities.
But why? you may ask. If the corporate platforms, services, and tools are working fine, why put any effort in changing? It’s easy to fall into the trap of believing our actions are of no consequence, and that compromises made along the way don’t accrue debts. Over the last decade, people have given corporate digital giants (aka “Big Tech”) immense power in society. While it has already been abused in many ways, more concentrated power means more abuse.
It’s largely a matter of personal responsibility on where you want to draw the line. Maybe it suits you to simply focus on preventing unwanted intrusion to your important accounts, or you could be willing to invest time and resources to do everything within your power. Your goals and aspirations are important to consider. Sometimes a small bit of effort can be strategically used to get the maximum benefit, others like to dedicate lots of effort over a significant amount of time. Ultimately the best moves are the ones that get the best impact with the effort and time you’re able to expend.
This overview is intended to be a starting-point for someone interested in reducing what sensitive information is shared about themselves, and keeping their systems safer from unwanted intrusion.
More Great Guides:
It may seem redundant to list other guides with similar information. Every project is going to have it’s own perspective, prioritization, and level of detail. If this guide is not to your liking, I would hope that one or many of these will suit your needs.
- Surveillance Self-Defense
- The New Oil
- Getting Started: Basic Personal Cybersecurity for Everyone
- Cybersecurity – What We Do
- Ninja’s Guide to the Internet
- A Good Privacy List
- Restore Privacy
- 10 Basic Steps to Digital Privacy
Contents
…More is to come!
The Regular Audit
I’d like to introduce you to the concept of a regular security audit. Instead of trying to reinvent your entire digital life overnight, it can be helpful to set aside some amount of time to make gradual changes, or to spend dedicated time solving a particular problem. This can help you transform a giant task over time, without too much immediate disruption to how you currently do things.
You can commit to whatever time interval works for you. It could be monthly, quarterly, or even yearly is worth considering over never at all. This can help you budget the time you’d like to spend on making changes, as well as help you keep an eye out for things to address later.
One helpful strategy would be to tier specific practices to certain intervals. For example making sure to run updates more regularly, but worry about changing passwords on a less frequent basis.
A hypothetical plan could look like this:
| 📆 Interval | ✅ Task |
|---|---|
| Weekly | Running Updates |
| Weekly | Cleaning your inbox |
| Weekly | File Backups |
| Monthly | Changing important passwords |
| Monthly | Deleting unused apps & extensions |
| Quarterly | System Backups |
| Quarterly | Checking for breaches |
| Quarterly | Helping others make changes |
| Yearly | Complete password rotation |
| Yearly | Online footprint inspection |
Why? Committing to a regular plan can help correct errors and keep you accountable. It also gets you focused on more proactive actions instead of always playing catchup.
The PEBKAC Vector
The easiest way for someone or something to infiltrate your accounts and systems is your own capacity to make a mistake. Hence the, Problem-Exists-Between-Keyboard-and-Chair vector. (That’s you!) One of the more obvious examples is how much people have been trained to share intimate details of their lives on corporate social media. Beyond just embarrassment, a lack of proper precautions can lead to having your entire system compromised. Consequences of that can range from mild regret to financially devastating.
Phishing Attacks
Phishing is when communications are sent out to trick a person to accidentally load a program, or divulge specific information. Phishing is very effective when combined with other attacks. The more someone (or something) can learn about you, the more effective phishing messages can be tailored to you. It is not out of the question that voice cloning, and other generative AI tools will be used to impersonate trusted contacts.
From A Non-Combattant’s Guide to Cyberwar
There are many different ways [phishing] can be carried out:
E-mail: one kind of attack is an urgent email that requires you to immediately click a certain link. That link will then present a fake log-in form disguised as a legitimate site. This could be used to steal your credentials. If the site itself has a vulnerability, merely clicking the link itself could be enough to compromise your account.Attachments: any file sent your way may be more than meets the eye. There are a variety of methods that allow a file that’s opened to either run as a virus, or send your data elsewhere.
None of this is exclusive to e-mail.
Messaging apps, and online communities can all enable the same problems.
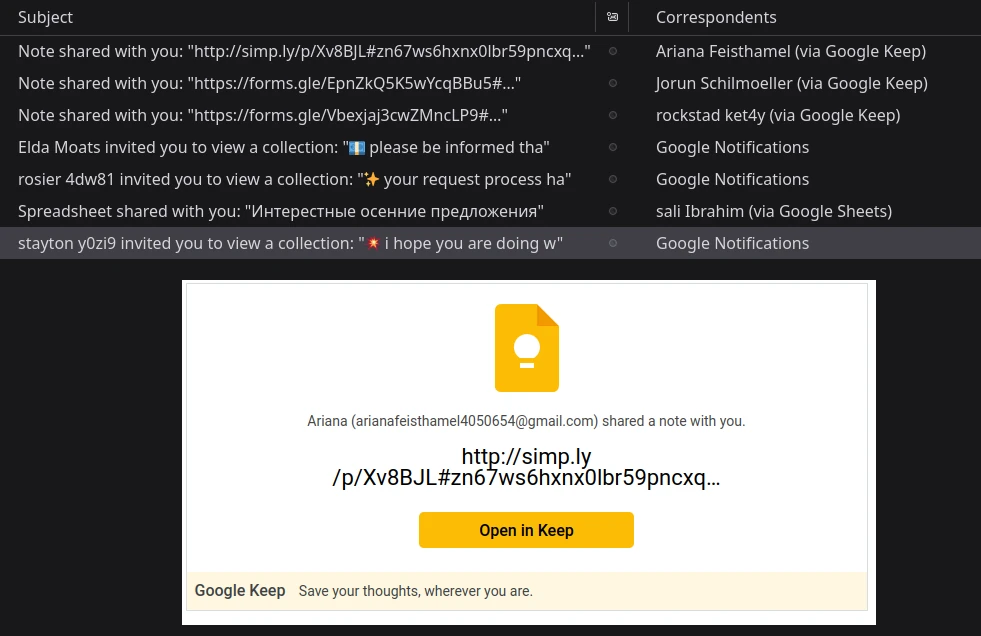
The line between spam and phishing is very blurry
Sometimes, an adversary being able to figure out which accounts are yours is enough to get very useful information, or to break into already compromised accounts. Other times, getting you to run some malware can give up complete control of your system. The best defense is to be aware of phishing, and take precaution before opening links or attachments.
Video: Protect Your Devices From Hackers – Don’t Get ‘0wned’ by AJ and the Electronic Frontier Foundation
For each channel, a purpose.
Reflect on how and in what way your trusted contacts will interact with you. Having separate email address(es) for different purposes can help filter specific messages for you, this will help you know if a particular message is genuine or not. Very often services will give you the option to enter a code instead of clicking a link, which is helpful in this situation. If you’re sure you must click a link, it can be worth copying it (with a right-click, or long touch) first, then inspecting it yourself before opening it.
Even something as simple as keeping in mind who tends to give you a phone call and who else prefers to use an end-to-end encrypted messaging app. If someone is reaching out to you in an unusual way, that can be an indication that something isn’t right. This applies to workplaces too, it can be a good idea to avoid mixing your career with your personal life, having an account for each can keep things separated.
Big Tech Services
Another way you may be outright, voluntarily handing out your information is when using cloud-driven and/or non-free software and services. Moving your data to your own devices, or at least to services run without vendor lock-in.
Disentangle Yourself from Cloud Platforms
There is no cloud, just somebody else’s computer!
Many online tools are just a service as a software substitute. This means that while you gain the convenience of sophisticated technologies at scale, you will also be unable to choose the terms of your computing. Simple things like using your own software like LibreOffice or Inkscape to create media allows you to keep your information under your own control. By not relying on external services for creating documents, presentations, or even notes you can go a long way to help reassert your own autonomy.
Choosing how you use social media will also have a significant impact. If you’re willing to put up with some inconvenience, it can be worth using alternate front ends for mainstream services to browse without being directly associated with an account. This can definitely help those who want to break away but don’t want to miss out on important information.
Online Footprint
Take Control of your Social Media
Being deliberate with your social media privacy settings is very important. Understand what features are available, and what it means for who can see what.
- Who can see posts you make?
- Is your profile searchable by site-members or anyone?
- Does someone have to request access to see your information?
It’s important to consider what you’d like to be public, vs what is best left offline.
The best way to protect information is to never record it in the first place!
Find Yourself in Search Engines
You can see how easy it is to get information on you by performing your own searches. Given that search engines will make an attempt to find results relevant to you, it’s worth trying multiple search engines rather than making assumptions off a single search. Including details about yourself may help narrow the results.
Consider Alternate Identities
On other platforms, you may have an identity that isn’t your real name. It’s generally a good idea not to repeat usernames across platforms unless the intention is for them to be publicly associated.
Close Dormant Accounts
If you no longer use a service, you may want to consider closing the account if the option is available. If nothing else, it ties up another loose end.
Privacy Policies
Digital products and platforms will have a published privacy policy that ideally outlines what information is collected and how it’s used. They will vary in content, clarity, and detail.
For online platforms privacy policies can help you understand:
- What information the platform collects
- If your information is being shared with or sold
Another document is a warrant canary. A warrant canary is a document that explains that the organization hasn’t received any requests for information from governments and/or law enforcement agencies. It’s a useful thing to have, because law enforcement agencies will sometimes gag providers from informing their clients, or even stakeholders.
“Two government officials who spoke on the condition of anonymity said the Justice Department obtained an individualized order from a judge of the Foreign Intelligence Surveillance Court last year. Yahoo was barred from disclosing the matter.”
Yahoo Said to Have Aided U.S. Email Surveillance by Adapting Spam Filter
Legislative Protections
Depending on your jurisdiction, you may be entitled to privacy protections. Notably, EU Citizens are covered by the GDPR which grants outlines regulations for organizations handling data deletion requests from individuals. It is worth being familiar with what privacy protections exist (or don’t exist) in your locale.
Account Security
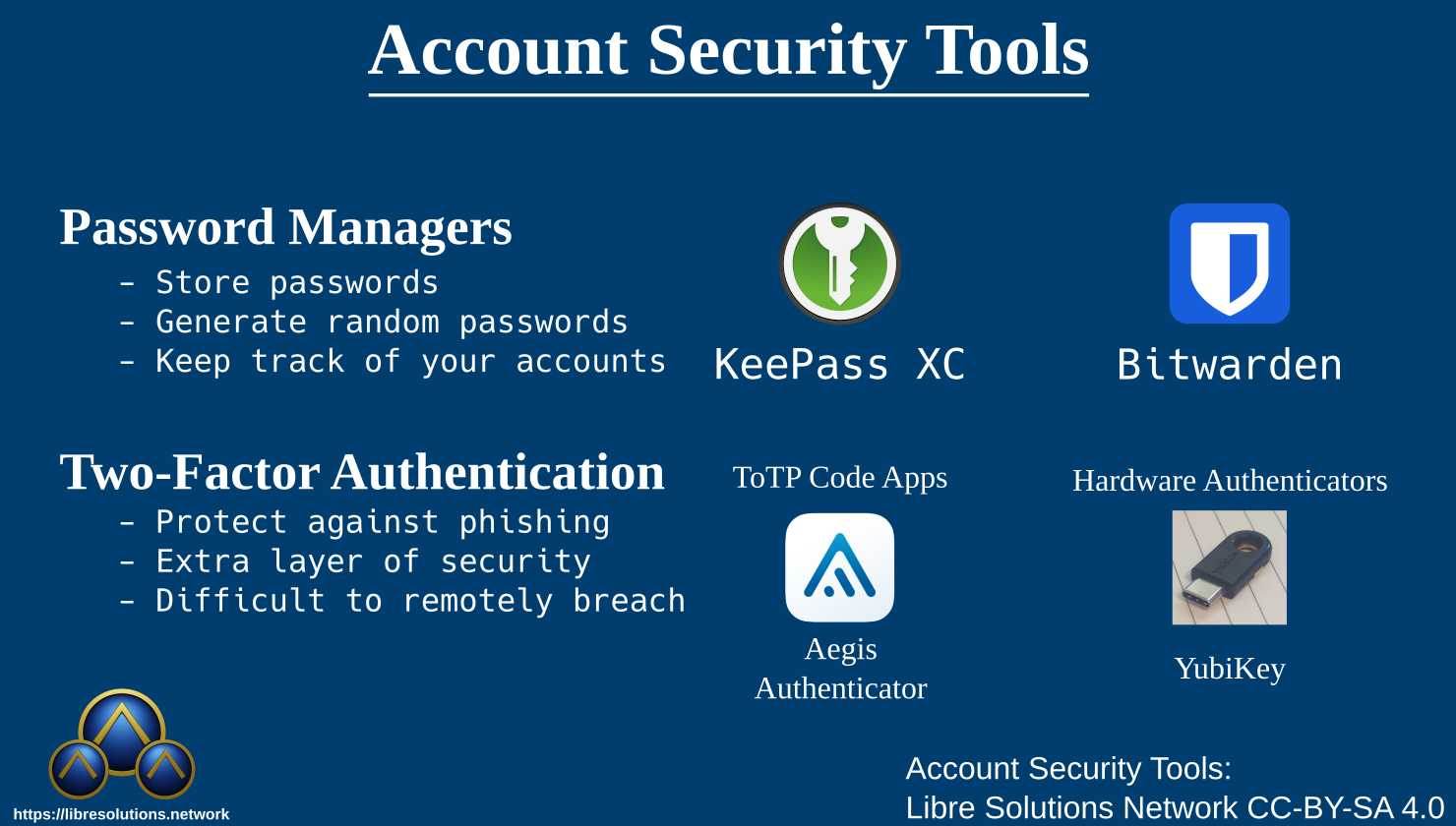
Using a Password Manager
While a notebook of passwords can be lost or stolen, there are digital means to keep track of accounts and passwords. Conveniently, some managers have integrated browser extensions that can make it easy to log in with stored passwords. These tools can go a long way towards improving your account security a lot easier to maintain.
Two password managers that I’ve used:
- KeePass XC (Offline)
- Bitwarden (Self-Hostable)
Long & Unique Passwords per account
Why? So that one account breach doesn’t spread to others.
Reusing passwords means that if your password is found in a data breach or hack, it can be used to gain access to other accounts.
Using a password manager can help you generate significantly longer passwords that are significantly harder to break, and may be more random than what you can come up with yourself.
Learn to develop good password management practices
Turn on either ToTP or hardware two-factor authentication, where possible
Why? By adding two-factor authentication you significantly raise the difficulty of attacks on your accounts. This can also buy you time to reset your password if it’s stolen. Multi-factor authentication is very important for protecting important accounts.
Unique e-mail addresses per account
Why? To make phishing campaigns much easier to identify.
Some e-mail providers support adding additional words to your email. For example you may be able to use +shopping at the end of your email as: name+shopping@example.com. This is good for filtering mail, but makes your alternate e-mails potentially discoverable.
If you’d like unique e-mails forwarded to your own e-mail address, an e-mail forwarding & aliasing service like firefox relay or addy.io can help. Many people will already have multiple e-mails from different providers, some of them may support aliases or disposable addresses.
Email is something that’s critical to get right. Almost every online account allows for accounts to be recovered (or stolen!) through email. This means that it’s the most important account to secure. Rotating your e-mail password more often than other accounts can definitely make a difference in the long run.
Beyond just being able to steal accounts, a hijacked email can also be used to spread scams and malware to others. Taking account security seriously is important!
Choose a Great Provider
Choosing a provider can be difficult. Even when one finds a great one, it’s not worth entirely relying on a single provider. If you run your own website, e-mail hosting can sometimes be included with web hosting. Of course, there’s always the option of running it yourself. That however, has its own challenges, but there are many advantages.
Email Provider Recommendations:
- E-mail providers - which one to choose?
- 10 Best Private and Secure Email Services for 2023
- Finding a Privacy-Friendly Email Provider
- Privacy Guides - Email Services
Criteria to consider:
-
Privacy
There are limits to how private e-mail can be, but it’s at least worth selecting a provider that isn’t profiting off scanning your mail.
Things to consider for privacy:- How long the provider has been in business
- Reputation of the provider
- Jurisdiction
- Business model and funding sources
- End-to-End Encryption
-
Features
Different options may have some variation in offerings. Important features can be:
- Webmail
- Storage size
- Custom Domains
- Disposable aliases
- Multiple accounts/mailboxes
- Encryption / PGP Support
- Client (IMAP & POP) Support
- Forwarding and Filters
I personally believe the best-case scenario for mass e-mail providers are responsibly run local non-profit enterprises. As online communication has become more central to people’s lives, competitive local infrastructure needs to take a more central role. While on the total other end of the spectrum, there also needs to be a place for less personal, but still quite small, providers that operate indiscriminately. Both have a very important place in safeguarding online freedom from a variety of threats.
Email Encryption
Every e-mail provider is going to market itself as secure. Secure from what? One may ask. Security is about proactive measures taken against particular problems. Nothing is 100% secure. Many security features proudly proclaimed by big tech services are really just about protecting information in transit as it goes from your machine to theirs. It’s very difficult for a provider to protect you from themselves, even when there’s desire to. There is always a degree of trust involved with hosting your data on somebody else’s computer.
Domestic government (and corporate) surveillance is a serious concern as well. Many of us in the so-called “Free World” have to be concerned about the 5 prying eyes. With all this in mind, I would never put too much faith email security guarantees. Even in the best of circumstances,treat e-mail like you would a postcard in the mail; not for anything particularly sensitive or private.
Strategy 1: Inbox Level
There are many end-to-end encrypted (“zero knowledge”) mailboxes provided by larger privacy-focused email providers. How it works is that in addition to your emails being secured in transit, they are also encrypted when they are stored. This means that as long as your account/password are secure, your email’s content can only be read by you. This often comes at the cost of lack of third-party client support.
This strategy has advantages, but mostly its ease-of-use. It saves you the time of having to manage your own encryption keys, meaning that others should be able to send you encrypted emails right away. The downside of this strategy is that you’re still placing a significant amount of trust on the provider, especially if you’re using it for sensitive information.
Strategy 2: Message Level
When using your own email client, you can choose to proactively encrypt emails with PGP. For recipients who’ve already setup their keys, some clients will be able to auto-discover the correct key for you so it can be fairly convenient. This strategy ensures that the email is secure as long as the recipients keys are, from all other parties. If your recipient already publishes their PGP key. (Here’s mine)
Metadata headaches
Regardless of which strategy you use, due to how e-mail works it’s impossible to conceal who you are sending it to, and many other details. Encrypted mail will protect the contents of the mail, but not extra information like when it was sent. For those who absolutely need to keep their contacts a secret, like investigative reporters, there are better options than e-mail.
Using an e-mail Client
Using Free Open Source Software clients put you back in charge of your mail. While webmail and apps can be very convenient, they can often be very opinionated on how you should interact with your mail. Mail clients are a very important tool. Some will provide privacy features like blocking e-mail trackers, and other useful tools like custom filtering.
Instead of leaving your mail on a server forever, you can move them to your computer for offline access. Every client will have its own features, but having the capability to encrypt emails with PGP is a non-trivial advantage.
I’m a huge fan of Mozilla Thunderbird though there are other e-mail clients, Privacy Guides has an excellent list of recommendations.
Configuring Your Client
It may seem intimidating, but if you have an uncommon mail provider, or roll you own email you may need to configure your client. This requires a few more options than just a username/password. To understand what the options mean you have to realize that you’re setting up two things:
-
Incoming Server:
Which needs:
- The mail server’s hostname (such as pop.example.com)
- Choosing either IMAP or POP as the protocol, this changes how the server handles mail that’s delivered.
- The port number the server is running on
- your email & password
- Security settings
-
Outgoing Server:
Which needs:
- The SMTP (Simple Mail Transfer Protocol) server’s hostname
- The server’s port number
- Your email & password
- Security settings
You’ll want to consult your e-mail providers documentation for the specific values. Contacting customer service may help. These settings are what’s required to configure any mail client, though some will be able to fill in some of the details when you provide your email address.
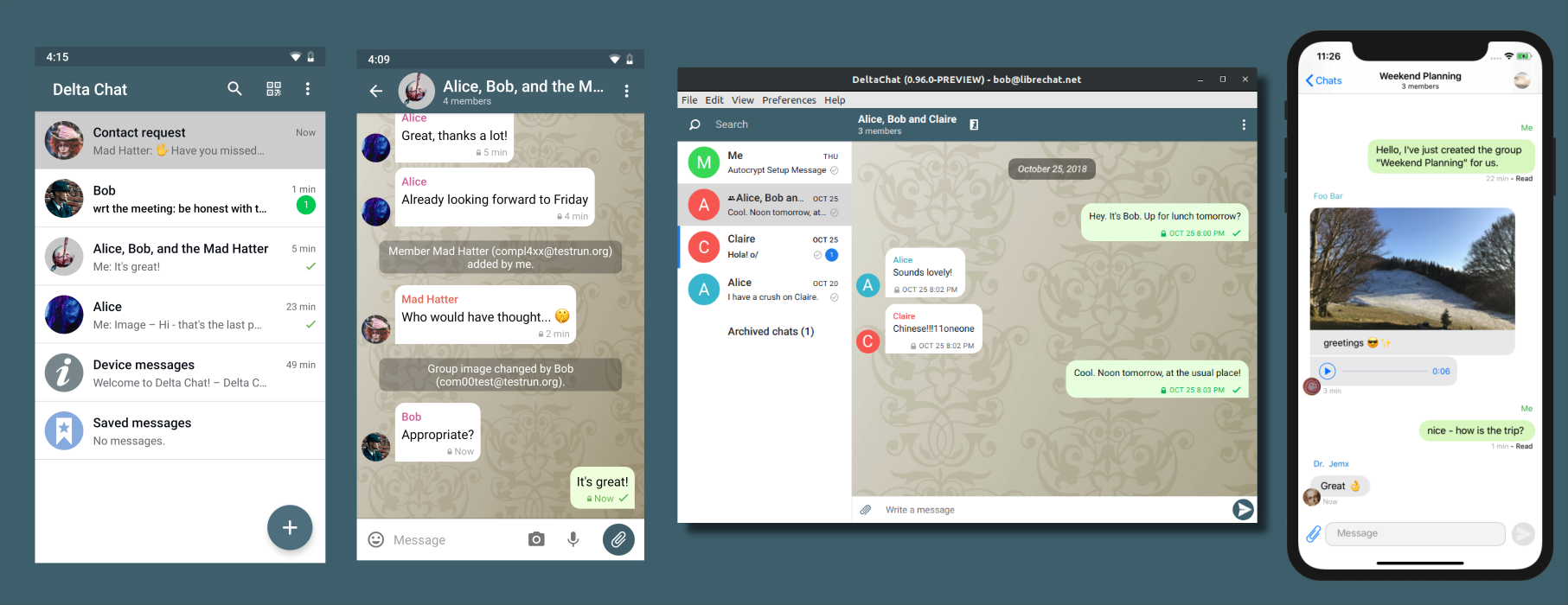
Delta Chat
Delta Chat is a mail client that looks and functions as an end-to-end encrypted messaging app. It’s an absolutely brilliant technique. Despite none of my contacts being (currently) willing to take it seriously, I actually believe that delta chat is one of the more underrated online messengers.
In theory, it should be very easy to adopt because it doesn’t require anyone to create any new accounts. It handles encryption key management for you, and uses your own inbox for storage. Of course, it can also send regular emails to those who don’t have it yet. For those who find signal requiring a phone number to be too much, I consider delta chat a must-have.
Inbox Cleaning
Junk mail piles up. Over the years, it can be easy to accumulate more and more spam and incoming mail that becomes unmanageable. This causes a lot of people to essentially ignore their e-mails all-together. If you’re not quite at the point of just abandoning that particular email and starting fresh, there’s a lot you can do to reduce the amount of unsanctioned messages.
Folders and Filtering
Odds are, a lot of regular incoming correspondence is expected in advance. This means that you can create sub-folders for particular domains, and use filters to sort your mail for you.This can keep the important stuff at hand, while allowing you to sort through the rest at your convenience.
Unsubscribe Without Mercy
Getting your email added or removed from marketing lists can really add-up over time. Reducing your incoming emails to what you specifically want can make a massive impact.
You can clean a busy inbox with this process:
- Find an example of something you no longer wish to receive
- Hit the “unsubscribe” button (usually near the bottom) on the email and get removed from the list
- Search for messages from that sender and delete them all
- Repeat every so often
Eventually, you’ll find you’re entirely free of unwanted incoming e-mails except for outright spam.
The Spam War
If you’re getting a great number of spam, it’s a sign that your email has appeared on many kinds of lists. Not having it published publicly can help, but fighting spam is a team effort. It’s worth your time to report egregious examples, but eventually you’ll want to setup your own filters for it. Where possible, if you have a filter that’s working well, I’d recommend having it also mark the message as spam.
Both Canadians, and Americans can report spam to law enforcement.
Trackers
There are two common types of e-mails you can send/receive. Plain text, which as the name implies is just text and is therefore entirely free of trackers. Emails can also be HTML, like web pages. This allows for them to look appealing, include images, and unfortunately trackers!
When you load an e-mail that loads content (like images) from a remote server, those assets can be used to send information. This can be used to get all kinds of engagement stats about how even you as an individual respond to particular messages. A troubling consequence of this is that those running phishing campaigns are able to use that information to come up with more compelling scams.
Browsers
You may be reading this in a browser. As you likely are aware, a web browser is a powerful program that displays & runs web pages and web applications. For many, it’s their primary gateway to the world wide web as well as the internet as a whole. Being complacent about what browser(s) you’re using is a surefire way to put your information in the hands of questionable external forces.
Understanding the Web
A good place to start is to refresh your understanding of what the web actually is. Like many things in our technological landscape, it wasn’t built in a day, or even by a single person. It’s an amalgamation of the work of many different people, institutions, and even governments over time. I’m very passionate about people choosing to take an active role in shaping cyberspace. Collectively, we do have a real impact on the future of the World Wide Web.
To begin, we have to start with the simplest of web pages. These are static web sites that display a set amount of text, images, or media.
Far from being mere hypertext, the web now includes multimedia applications. Web 2.0 was when web sites became dynamic. Forums, Wikis, and even the first social media sites were dynamic because user interaction fed into a database that was used to generate web content. The earliest of these could work without many (if any) scripts at all, and were processed by the web site’s back-end software.
A web page can load real-time data from an online service, and/or stream audio and video. Because of this, the browser is the primary tool in many people’s digital life. Like anything else, this includes a variety of risks and trade-offs.
The addition of more content and features to the web has made browsers themselves increase in complexity significantly. In theory, a browser would only need to support downloading the page, and displaying the text on it. As the web has evolved, browsers now support all kinds of multi-media, interactivity, and online gaming.
While this isn’t necessarily news to you, what is worth understanding is that all of these additional features have meaningful trade-offs when it comes to privacy & security. There are those who yearn for a return of the days of just clean pure hypertext. If that sounds like something you’re interested in, gemini is right up your alley. For the rest of us who would like to enjoy a wide variety of modern enhancements to the web, there is much to account for.
Surveillance
In many ways, it helps to think of much of the Web as a street filled with surveillance cameras. Without making significant effort, it’s trivial for those watching to keep track of where you go on a regular basis. In addition to this, the places you visit themselves may also be spying on you in exchange for a pithy sum.
Cookies & Storage
It’s pretty useful to be able to log-in to a website. It’s also very handy for the server to save some additional information on your end so when you return you can continue as normal. Using sessions is how servers keep track of who they’re talking to. Naturally, if you divulge more information about yourself to a particular service, the more that information can be corroborated with other data points. Without saving cookies, log-ins and site settings would be lost immediately, but that doesn’t mean you need to hold onto them forever.
Scripts
Either scripts from the site itself, or remote scripts pulled in from other services can do a wide range of things to try to uniquely identify you. On the other hand, many sites will not work at all and refuse to display something as simple as an article. Many tracking blockers will block all external scripts, but others will make exceptions that keep certain mainstream sites working.
The best practice would be to block any unnecessary scripts. There are many add-ons that can make this easier. “Unnecessary” can be a very broad categorization however, in some cases you may consider it worth blocking any and all scripts everywhere. This is the recommended setup when using the Tor Browser, because scripts can do many things to de-anonymize a visitor.
Sadly many of these invasive scripts have been thrust on the public without much alternative. As a web developer, it may be tempting (or even good for your resume) to develop using the latest fancy script frameworks, it’s important to remember that you can maintain all the advantages of dynamic web sites without it. When security and privacy of your users is paramount, it’s something worth considering.
Fingerprinting
Now that you’ve put in the effort to properly mitigate unwanted data leakage. There’s still another nasty problem. If you require perfect anonymity online, it’s worth understanding that your browser fingerprint can be used to uniquely identify you online. This is a problem, but it’s one not worth working on at the expense of protecting important information.
Choosing a Browser
DigDeeper.club has an excellent if troubling post on browsers. Unfortunately the major take-away is that the situation is very dire:
The only reasonable choice is Pale Moon. Or, just try wean yourself off the modern web by sticking to websites such as the ones on Neocities, wiby.me, etc. which are functional in NetSurf or terminal browsers. I hate to kill the positivity of yet another summary, but if reality forces me to - what can I do?
(emphasis mine)
If you require using the modern web (ie. most “normal” websites) I recommend reading through the guide carefully and choosing what strikes the right balance for you.
Reading through the browser guide leaves the impression that a serious web & browser renewal is something people from all walks of life should strongly consider.
The root of the problem is two-fold:
- Additional features on modern web sites introduce additional privacy risks
- To support these features, browsers themselves become more complicated to support, maintain, and validate
I intend to follow-up on this particular section, and I think it’s important to think-through how things should be done. This is one of the many reasons I emphasize more people getting involved, rather than let governments and corporations dictate it for us.
The More the Merrier
Because browsers are tools, it doesn’t often make sense to entirely limit yourself to a single one. There are some advantages to using different browsers for different “spheres” of your life. Above all, it’s best to understand why you’re using a particular browser for a certain task. If you’re really in love with a particular browser, you may be able to use multiple profiles with different settings in mind for different uses. Even something as simple as having separate bookmarks for each profile would make it easy to stay consistent.
In all cases you’ll likely want to alternate browsers for different tasks, with at least one clearing cookies/logins/history on reload. You may also want to search for a hardening guide for whatever browser you choose, depending on your particular needs. It can help to have a hardened browser for most of your basic web tasks, with exceptions made for sites/services you need/trust and alternate ones for other things. Compartmentalization can go a long way especially with many browsers offering built-in VPNs. More on VPNs later
Hardening
Here is an excellent firefox hardening guide for firefox.
Hardening is the process of changing settings for particular privacy and security. Sometimes these changes include disabling tracking from the program itself! A good place to start is opt-ing out of any telemetry or analytics reporting. Then I would generally recommend taking the most extreme settings you can bear day-to-day, and consider increasing as you adapt. Some more ‘extreme’ changes would be disabling WebRTC to protect your IP at the cost of some real-time applications breaking.
Many of these changes will either be in your browsers settings panel or additionally about:config on firefox based browsers. On desktop Firefox Arkenfox’s user.js file is a highly-recommended change for getting the most optimal settings. This alone may be a good reason to pick a firefox or its derivatives over google chrome and its derivatives.
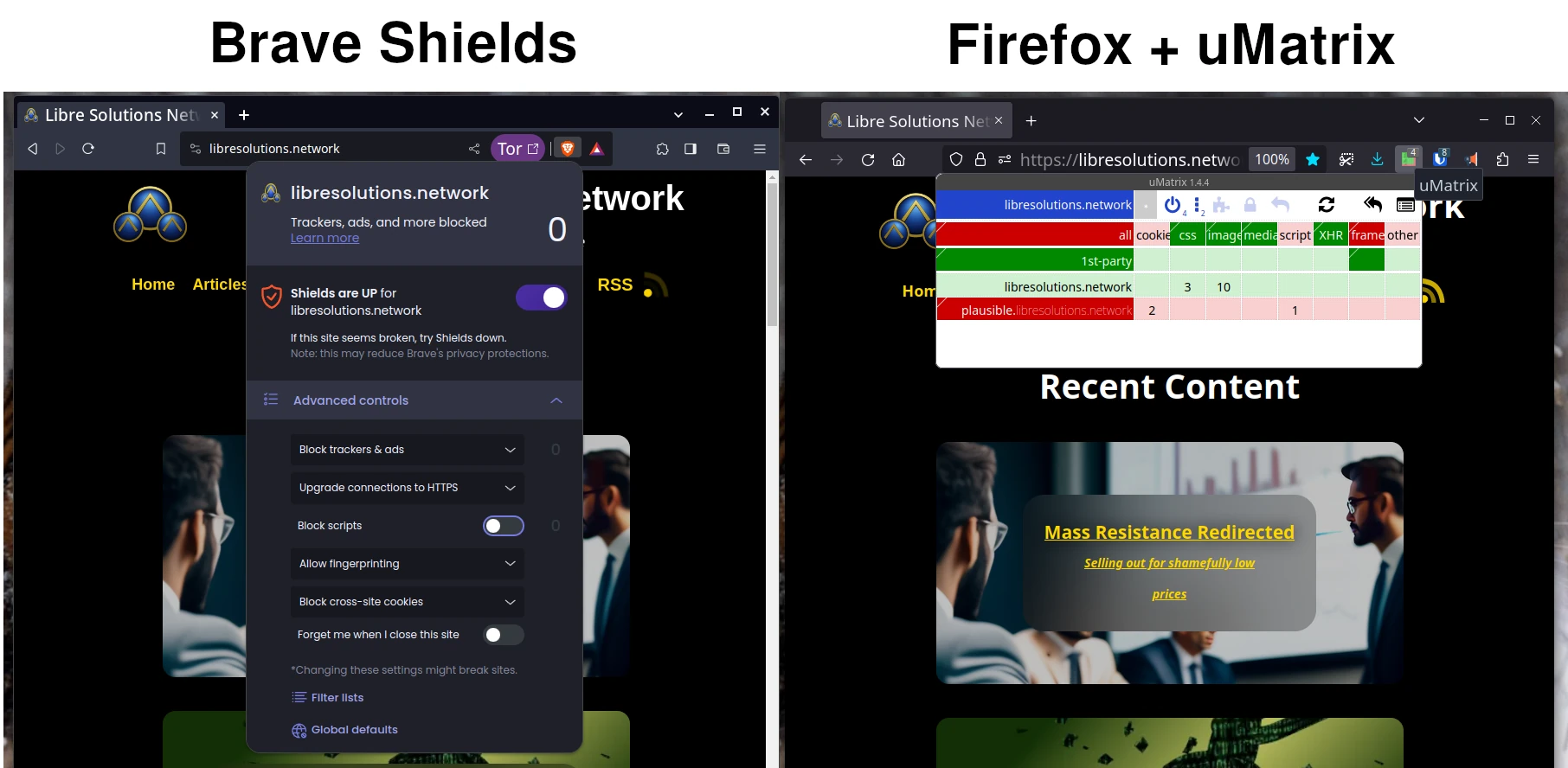
If you’re using brave shields you have an intuitive interface for being as strict as possible. It also has the advantage of being built into the browser for additional performance gains. On other browsers uBlock Origin is the go-to add-on for having complete control over what resources sites can access. Learning how to use these tools can do a great deal of good.
Browser Add-ons
A browser can feel very limiting without many essential add-ons. Ad-blocking is de-facto necessary for browsing a great deal of the web to salvage some of your time and attention.
I’ve personally used:
-
It’s great to have full control over requests on a site-by-site basis. It takes a bit of learning, but is a very powerful tool that I’d love to see built-in to new FOSS browsers. By blocking specific kinds of remote requests across the board, you can disable all third-party ads.
-
A very useful tool for redirecting all kinds of mainstream social media links to dedicated (somtimes self-hosted!) web proxies.
-
See Account Security
-
If you’re going to allow remote scripts, it can be handy to proactively cache them, so that you’re not constantly being tracked by loading them on each visit to separate sites.
Network Security
Computer networks are fascinating things. The ability to link two devices over a long distance to accomplish sophisticated tasks is what makes much of our modern computing environment seem outright magical. Of course, where there’s power there’s also danger, the massive capabilities of networked systems vastly complicate the challenges of securing systems. To do the best you can, it’s important to have a basic understanding of computer networking and take reasonable precautions.
An important place to start is to understand that every data connection relies on a physical connection on some form. You can relay data between two computers by linking them directly, or use routers to share data with networks outside your own local network.
Local Area Network (LAN)
Odds are, you likely have a modem/router machine in your house. It runs your local network and also provides a WiFi access point to wireless devices. This allows for all devices on the network to use the router to connect to your internet service provider (ISP).
The importance of protecting your local network can not be overstated. Usually, your router will have a web admin access that you can use to ensure only devices you’ve authorized are connected. Managing access to your local network is your first-line of defense against many nefarious threats. For low-value targets, physical access may be sufficient, but for high value targets or high-traffic locations, the considerations differ.
WiFi
Use a strong WiFi password. Any device connected to your WiFi may as well be wired directly into every other computer or device on the network. Due to their nature as broadcasted signals, wireless networks are difficult to properly secure and may be vulnerable to unintuitive attacks. An open network, or even a weakly secured one creates opportunity for spying, compromise, or infiltration. There are many ways in which WiFi signals can be intercepted or jammed, in most cases it’s best to run sensitive systems over a direct wired connection. In situations where WiFi is needed, there are options such as segregating wireless clients from the same network. An option is to have the wireless network entirely disconnected or to relegate different devices to separate VLANs.
Router
Routers are what move messages between networks. Your router may connect to an internal modem that acts as a gateway to your internet service provider to connect to the rest of the Internet. Like any device on your network, it’s very important to ensure that you’re able to choose a router that has up to date software and isn’t compromised. Given its important role in your network, having a router you can trust is arguably one of the most important aspects of network security. At least in Canada, the status quo for many customers is to rely on a single device managed by their ISP, for better or worse. In some cases, people will decide to buy their own device running software that they trust and is maintained, to separate their network from the ISP provided router.
Firewalls
A firewall is a useful tool to manage connections that come in the network. While it’s worth remembering that Firewalls Don’t Stop Dragons, they are a vital tool in making connecting to the Internet without necessarily giving complete access. A firewall accepts incoming connections and ignores any connections that aren’t explicitly allowed. Firewalls can be software on a router, such as the one included in many ISP-provided routers or a dedicated device. A go-to recommendation for custom firewall software is OPNsense which is built on pfsense.
Domain Name System (DNS)
Every site or service online has a publicly routable IP address, to connect to it your browser or applications need to get the correct IP address from the service’s domain. This means that DNS is effectively a real-time system divulging what you’re connecting to, how often, and when. One solution to resolve this is to encrypt your DNS queries. To do this, you’ll want to make sure your devices and browsers are configured with a deliberately chosen DNS provider. Encrypting your DNS requests is as important as not making them to a malicious or negligent entity.
There are many providers, but this only protects you from protecting onlookers from monitoring your requests, the provider may still have that information. Another important technique is to cache your requests with a recursive DNS resolver. This means that your devices will all connect to a resolver you run yourself, it then asks another DNS provider for the information and remembers it for a short period of time. Pihole is a fairly popular option for achieving this, and it also includes ad-blocking features.
Why?
…for many actors, metadata is far more valuable than the content. From a privacy perspective, DNS seems to be one of the most under-appreciated aspects of protecting oneself.
In many ways it is because most good VPNs will handle DNS as well, but there are other considerations.DNS can also be set at the application level. Browsers, for example, will have their own DNS settings. Most major browsers now support DOH, which is a very convenient way to encrypt your browser’s DNS queries. For encrypting all of your system’s DNS queries you may want to consider using DNSCrypt.
End-to-End Protection
For a connection to be fully secure, it needs to:
- Reach its destination
- Not be modified or interfered with
- Have reasonable protection against being identified
This turns out to be quite a high bar, even encryption often only protects the content of communications but it can be much easier to observe who’s communicating with who, how often, or other metadata. You can do everything right on your end but if you connect to a malicious or compromised service, you can have problems. Man-in-the-middle attacks are even possible with modern encrypted websites, anyone able to use a certificate recognized by your device can do many malicious things including deep packet inspection to effectively nullify most web encryption. Resolving this is much more complicated, and requires much more effort.
Proxies, VPNs & Darknets
For computer networks to work, every computer needs a public IP address. How this works in practice (with IPv4 usually…) is that your machine has a number that your router knows, which has a number your ISP knows, which is then shared with the rest of the internet. That last number is your IP (public) address. Using a VPN does two things: 1) encrypts traffic between you and the service 2) forwards your connections through one of their IP addresses.
Virtual Private Network are often seen as the solution to all online privacy issues. This is people being mislead by slick advertising. VPNs are very useful for accessing content that is blocked in specific regions or protecting your IP from being known by online services. There are many ways users using a VPN can have their IP leaked so it is essential to make sure you are using your VPN properly.
Your internet service provider (ISP) may not be trustworthy so you may want to use a VPN, it is important to realize that by using a VPN you are effectively transferring the risk of your ISP logging, tracking, censoring your information to that VPN provider. Like ISPs VPNs are businesses and it is foolish to assume they will put your needs as an individual or customer before the interests of their business.
Just like DNS providers, your ability to trust your VPN provider is quite important as well. Your ability to protect your information from them is just as difficult as masking your internet activity from your ISP. In addition to this, VPNs are prone to very unintuitive attacks. DNS leaks are when your VPN is working fine, but your DNS queries are being routed from your home IP address instead of the VPN providers, effectively unmasking you. Ironically, VPNs are often recommended in circumstances where you can’t trust the network, such as a public WiFi, but this is the exact scenario where a recent attack would allow somebody to reroute your traffic outside the VPN. A proxy is a simpler way of changing where your requests come from than a VPN, but has similar concerns.
Unless you plan to work entirely offline, you’re going to have to consider how you connect to the internet, and specific sites & services.
I would argue, that it’s more important these days to hide one’s IP address than it was in the past. Internet geolocation as only gotten more precise over time. Depending on the accuracy, someone may be able to identify your neighborhood.
There is no one-size-fits-all solution when it comes to VPNs. Just like email, there are many VPN services out there and you should choose the service that works best for you. Depending on which one you choose, you can benefit from an increased level of security when connected to networks you wouldn’t ordinarily trust. But this means you’re placing your trust in the VPN.
Consider your goals:
- Are you just trying to avoid disclosing your IP with sites & services you visit? Good VPNs & Proxies will suit this purpose.
- Are you trying to evade ISP-level censorship and connect to services that are online but inaccessible to you? This is what Tor was built for, potentially being difficult to identify is also a useful feature but is much less guaranteed.
- Or are you trying to connect to specific “hidden services” served anonymously?
Then you’ll need want to consider darknets like Tor or I2P.
Thank you taking the time to read this overview.
Any comments, questions or feedback would be appreciated.
Is this all there is to do? Of course not! I hope that this can be a good starting reference for those who don’t know where to begin.
Additional resources
Sharing is caring!
Please send this post to anyone you think might be interested.
If you haven't already, don't forget to bookmark this site!
You can always subscribe with the RSS feed or get posts sent to your inbox via Substack.